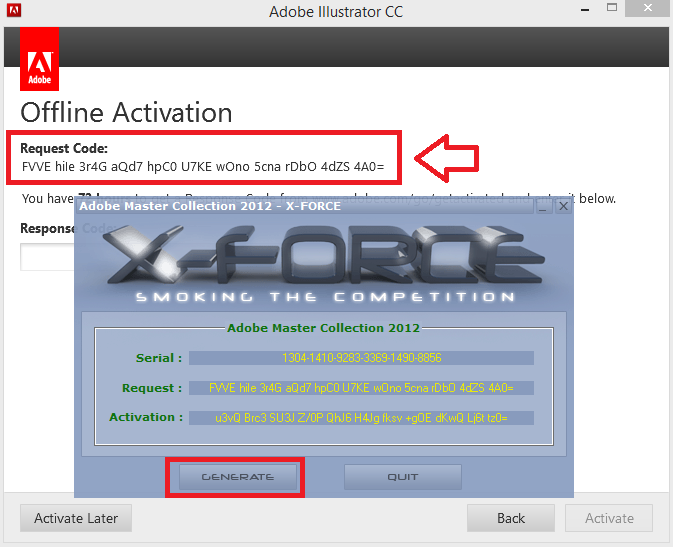
Adobe Offline Activation Response Code 401
Store share your files with uploaded. Learn more about our services videoAfter entering your e. Mail addres and receipt of your registration youll simultaneously receive your personal access data from us. This is always free of charge. View and Download Aficio MP 6002 user manual online. MP 6002 All in One Printer pdf manual download. Cisco ASA 5. 50. 0 Series Command Reference, 8. Cisco ASA 5. 50. 0 X Series Firewalls same security traffic through show asdm sessions Commands same security traffic To permit communication between interfaces with equal security levels, or to allow traffic to enter and exit the same interface, use the same security traffic command in global configuration mode. Counter Strike Source Compressed Pc Game. To disable the same security traffic, use the no form of this command. Syntax Descriptioninter interface Permits communication between different interfaces that have the same security level. Permits communication in and out of the same interface. Get a free email address from AOL now You no longer need to be an AOL member to take advantage of great AOL Mail features such as industryleading spam and virus. SmartPCFixer is a fully featured and easytouse system optimization suite. With it, you can clean windows registry, remove cache files, fix errors, defrag disk. CompTIA Security SY0501 Cert Guide Premium Edition and Practice Tests, 4th Edition. Adobe Offline Activation Response Code 401' title='Adobe Offline Activation Response Code 401' />Defaults This command is disabled by default. Command Modes The following table shows the modes in which you can enter the command. Command Mode. Firewall Mode. Security Context. Routed. Transparent. Single. Multiple. Context. System. Global configuration Command History. Release. Modification. This command was introduced. The intra interface keyword now allows all traffic to enter and exit the same interface, and not just IPSec traffic. Old Retro Games For Android. Usage Guidelines Allowing communication between same security interfaces enabled by the same security traffic inter interface command provides the following benefits You can configure more than 1. If you use different levels for each interface, you can configure only one interface per level 0 to 1. You can allow traffic to flow freely between all same security interfaces without access lists. The same security traffic intra interface command lets traffic enter and exit the same interface, which is normally not allowed. This feature might be useful for VPN traffic that enters an interface, but is then routed out the same interface. The VPN traffic might be unencrypted in this case, or it might be reencrypted for another VPN connection. For example, if you have a hub and spoke VPN network, where the adaptive security appliance is the hub, and remote VPN networks are spokes, for one spoke to communicate with another spoke, traffic must go into the adaptive security appliance and then out again to the other spoke. Note All traffic allowed by the same security traffic intra interface command is still subject to firewall rules. Be careful not to create an asymmetric routing situation that can cause return traffic not to traverse the adaptive security appliance. Examples The following example shows how to enable the same security interface communication hostnameconfig same security traffic permit inter interface. The following example shows how to enable traffic to enter and exit the same interface hostnameconfig same security traffic permit intra interface. Related Commands. Command. Description. Displays the same security traffic configuration. To specify a SASL Simple Authentication and Security Layer mechanism for authenticating an LDAP client to an LDAP server, use the sasl mechanism command in aaa server host configuration mode. The SASL authentication mechanism options are digest md. To disable an authentication mechanism, use the no form of this command. Note Because the adaptive security appliance serves as a client proxy to the LDAP server for VPN users, the LDAP client referred to here is the adaptive security appliance. Syntax Description Syntax Description. Syntax Descriptiondigest md. The adaptive security appliance responds with an MD5 value computed from the username and password. The adaptive security appliance responds by sending the username and realm using the GSSAPI Generic Security Services Application Programming Interface Kerberos mechanism. Specifies the Kerberos aaa server group, up to 6. Defaults No default behavior or values. The adaptive security appliance passes the authentication parameters to the LDAP server in plain text. Note We recommend that you secure LDAP communications with SSL using the ldap over ssl command if you have not configured SASL. Command Modes The following table shows the modes in which you can enter the command. Command Mode. Firewall Mode. Security Context. Routed. Transparent. Single. Multiple. Context. System. aaa server host configuration Command History. Release. Modification. This command was introduced. Usage Guidelines Use this command to specify adaptive security appliance authentication to an LDAP server using SASL mechanisms. Both the adaptive security appliance and the LDAP server can support multiple SASL authentication mechanisms. When negotiating SASL authentication, the adaptive security appliance retrieves the list of SASL mechanisms configured on the server and sets the authentication mechanism to the strongest mechanism configured on both the adaptive security appliance and the server. The Kerberos mechanism is stronger than the Digest MD5 mechanism. To illustrate, if both the LDAP server and the adaptive security appliance support both mechanisms, the adaptive security appliance selects Kerberos, the stronger of the mechanisms. When disabling the SASL mechanisms, you must enter a separate no command for each mechanism you want to disable because they are configured independently. Mechanisms that you do not specifically disable remain in effect. Program De Recuperare In Hernia De Disc there. For example, you must enter both of the following commands to disable both SASL mechanisms no sasl mechanism digest md. Examples The following examples, entered in aaa server host configuration mode, enable the SASL mechanisms for authentication to an LDAP server named ldapsvr. IP address of 1. 0. This example enables the SASL digest md. The following example enables the SASL Kerberos authentication mechanism and specifies kerb servr. Kerberos AAA server hostnameconfig aaa server ldapsvr. Related Commands. Command. Description. Specifies that SSL secures the LDAP client server connection. Specifies the LDAP server vendor as either Microsoft or Sun. Creates and names an LDAP attribute map for mapping user defined attribute names to Cisco LDAP attribute names. To specify the number of SAST certificates to create in the CTL record, use the sast command in ctl file configuration mode. To set the number of SAST certificates in the CTL file back to the default value of 2, use the no form of this command. Syntax Description numbersasts Specifies the number of SAST keys to create. The default is 2. Defaults No default behavior or values. Command Modes The following table shows the modes in which you can enter the command. Command Mode. Firewall Mode. Security Context. Routed. Transparent. Single. Multiple. Context. System. CTL file configuration Command History. Release. Modification. The command was introduced. Usage Guidelines CTL files are signed by a System Administrator Security Token SAST. Because the Phone Proxy generates the CTL file, it needs to create the SAST key to sign the CTL file itself. This key can be generated on the adaptive security appliance. A SAST is created as a self signed certificate. Typically, a CTL file contains more than one SAST. In case a SAST is not recoverable, the other one can be used to sign the file later. Examples The following example shows the use of the sast command to create 5 SAST certificates in the CTL file hostnameconfig ctl file sast 5. Related Commands. Command. Description. Specifies the CTL file to create for Phone Proxy configuration or the CTL file to parse from Flash memory. Specifies the CTL file to use for Phone Proxy configuration. Configures the Phone Proxy instance.