Trend Micro Officescan Activation Code
Top frequently asked questions How do I request a refund To request a refund, you must look up your order and then use the Request a Return option to submit. Navigation. Use this post to build a virtual desktop that will be used as the parent image or source image for additional virtual desktops. Theres a separate. Trend-Micro/Internet-Security/Screenshots/large/2.png' alt='Trend Micro Officescan Activation Code' title='Trend Micro Officescan Activation Code' />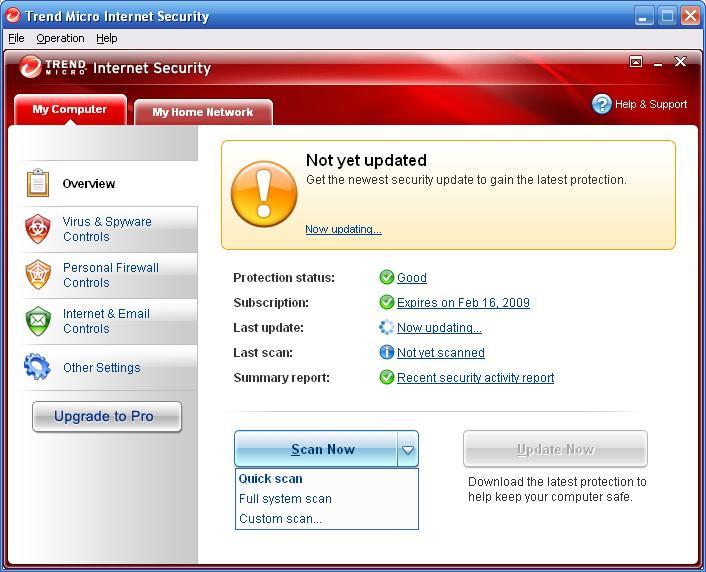 Enter your email address to subscribe to this blog and receive notifications of new posts by email. Vulnerability Summary for the Week of October 2, 2. The US CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology NIST National Vulnerability Database NVD in the past week. The NVD is sponsored by the Department of Homeland Security DHS National Cybersecurity and Communications Integration Center NCCIC United States Computer Emergency Readiness Team US CERT. For modified or updated entries, please visit the NVD, which contains historical vulnerability information. The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System CVSS standard. The division of high, medium, and low severities correspond to the following scores High Vulnerabilities will be labeled High severity if they have a CVSS base score of 7. Medium Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4. Low Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0. Entries may include additional information provided by organizations and efforts sponsored by US CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of US CERT analysis. Trend Micro Officescan Activation Code' title='Trend Micro Officescan Activation Code' />High Vulnerabilities. Primary. Vendor Product. Trend Micro Officescan Activation Code' title='Trend Micro Officescan Activation Code' />Description. Published. CVSS Score. Source Patch Infoersdata ersdatasystem. ERS Data System 1. Update. Request object deserialization. Download Swf Files With Mozilla Firefox. CVE 2. 01. 7 1. MISCEXPLOIT DBgnu binutils. Memory leak in decodelineinfo in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file. 2. 01. 7 0. CVE 2. 01. 7 1. CONFIRMhp applicationperformancemanagement. A potential security vulnerability has been identified in HPE Application Performance Management BSM Platform versions 9. The vulnerability could be remotely exploited to allow code execution. CVE 2. 01. 7 1. BIDMISCCONFIRMhp bsmplatformapplicationperformancemanagementsystemhealth. A directory traversal vulnerability in HPE BSM Platform Application Performance Management System Health product versions 9. CVE 2. 01. 7 1. MISCCONFIRMAUSCERThp bsmplatformapplicationperformancemanagementsystemhealth. An authentication vulnerability in HPE BSM Platform Application Performance Management System Health product versions 9. CVE 2. 01. 7 1. MISCCONFIRMAUSCERThp ucmdbconfigurationmanager. A potential security vulnerability has been identified in HP UCMDB Configuration Manager versions 1. These vulnerabilities could be remotely exploited to allow code execution. CVE 2. 01. 7 1. CONFIRMBack to top. Medium Vulnerabilities. Primary. Vendor Product. Description. Published. CVSS Score. Source Patch Infoapache geode. When a cluster is operating in secure mode, a user with read privileges for specific data regions can use the gfsh command line utility to execute queries. In Apache Geode before 1. CVE 2. 01. 7 9. MLISTartifex gsview. Artifex GSView 6. Beta on Windows allows attackers to cause a denial of service or possibly have unspecified other impact via a crafted. Possible Stack Corruption starting at KERNELBASE Raise. Exception0x. CVE 2. CONFIRMartifex gsview. Artifex GSView 6. Beta on Windows allows attackers to cause a denial of service or possibly have unspecified other impact via a crafted. Reviews Of T-Tapp Exercise Program. Data from Faulting Address controls Branch Selection starting at mupdfnet. Incremental. Save. File0x. 00. 00. 00. CVE 2. 01. 7 1. CONFIRMartifex gsview. Artifex GSView 6. Beta on Windows allows attackers to execute arbitrary code or cause a denial of service via a crafted. Read Access Violation on Block Data Move starting at mupdfnet. Incremental. Save. File0x. 00. 00. 00. CVE 2. 01. 7 1. CONFIRMblogotextproject blogotext. Stored XSS vulnerability via a comment in incconv. Blogo. Text before 3. Java. Script. If the victim is an administrator, an attacker can for example change global settings or createdelete posts. It is also possible to execute Java. Script against unauthenticated users of the blog. CVE 2. 01. 7 1. MISCMISCMISCMISCcfpaypal cpcontactformwithpaypal. The cp contact form with paypal aka CP Contact Form with Pay. Pal plugin before 1. Word. Press has CSRF with resultant XSS, related to cpcontactformpp. CVE 2. 01. 5 9. MISCMISCMISCcfpaypal cpcontactformwithpaypal. The cp contact form with paypal aka CP Contact Form with Pay. Pal plugin before 1. The Elder Scrolls Oblivion Patch 1.2. Word. Press has SQL injection via the cpcontactformppid parameter to cpcontactformpp. CVE 2. 01. 5 9. MISCMISCMISCcheckmkproject checkmk. CheckMK before 1. GUI crash report. CVE 2. 01. 7 1. CONFIRMCONFIRMegroupware egroupware. Stored XSS vulnerability in e. Groupware Community Edition before 1. Java. Script via the User Agent HTTP header, which is mishandled during rendering by the application administrator. CVE 2. 01. 7 1. MISCMISCfreedesktop poppler. In Poppler 0. 5. 9. NULL Pointer Dereference exists in Annot. Rich. Media Content Content in Annot. PDF document. 2. 01. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. In Poppler 0. 5. 9. NULL Pointer Dereference exists in the Splash. Output. Dev type. D0 function in Splash. Output. Dev. cc via a crafted PDF document. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. In Poppler 0. 5. 9. NULL Pointer Dereference exists in Annot. Rich. Media Configuration Configuration in Annot. PDF document. 2. 01. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. In Poppler 0. 5. 9. Object dict. Lookup in Object. Gfx display, Gfx go, Gfx exec. Op, Gfx op. Fill, Gfx do. Pattern. Fill, Gfx do. Tiling. Pattern. Fill and Gfx draw. Form calls aka a Gfx. CVE 2. 01. 7 1. CVE 2. CONFIRMfreedesktop poppler. The Fo. Fi. Type. C convert. To. Type. Fo. Fi. Type. 1C. Poppler 0. 5. 9. 0 has a NULL pointer dereference vulnerability because a data structure is not initialized, which allows an attacker to launch a denial of service attack. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. The Fo. Fi. Type. C convert. To. Type. Fo. Fi. Type. 1C. Poppler 0. 5. 9. 0 has a heap based buffer over read vulnerability if an out of bounds font dictionary index is encountered, which allows an attacker to launch a denial of service attack. CVE 2. 01. 7 1. CONFIRMCONFIRMfreedesktop poppler. The Fo. Fi. True. Type get. CFFBlock function in Fo. Fi. True. Type. cc in Poppler 0. NULL pointer dereference vulnerability due to lack of validation of a table pointer, which allows an attacker to launch a denial of service attack. CVE 2. 01. 7 1. CONFIRMgnu binutilsdecodelineinfo in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file. 2. 01. 7 0. CVE 2. 01. 7 1. CONFIRMCONFIRMgnu binutilsreadformattedentries in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file. 2. 01. 7 0. CVE 2. 01. 7 1. CONFIRMCONFIRMCONFIRMgnu binutilsprocessdebuginfo in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file that contains a negative size value in a CU structure. CVE 2. 01. 7 1. CONFIRMCONFIRMgnu binutilsbfdelfslurpversiontables in elf.
Enter your email address to subscribe to this blog and receive notifications of new posts by email. Vulnerability Summary for the Week of October 2, 2. The US CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology NIST National Vulnerability Database NVD in the past week. The NVD is sponsored by the Department of Homeland Security DHS National Cybersecurity and Communications Integration Center NCCIC United States Computer Emergency Readiness Team US CERT. For modified or updated entries, please visit the NVD, which contains historical vulnerability information. The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System CVSS standard. The division of high, medium, and low severities correspond to the following scores High Vulnerabilities will be labeled High severity if they have a CVSS base score of 7. Medium Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4. Low Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0. Entries may include additional information provided by organizations and efforts sponsored by US CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of US CERT analysis. Trend Micro Officescan Activation Code' title='Trend Micro Officescan Activation Code' />High Vulnerabilities. Primary. Vendor Product. Trend Micro Officescan Activation Code' title='Trend Micro Officescan Activation Code' />Description. Published. CVSS Score. Source Patch Infoersdata ersdatasystem. ERS Data System 1. Update. Request object deserialization. Download Swf Files With Mozilla Firefox. CVE 2. 01. 7 1. MISCEXPLOIT DBgnu binutils. Memory leak in decodelineinfo in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file. 2. 01. 7 0. CVE 2. 01. 7 1. CONFIRMhp applicationperformancemanagement. A potential security vulnerability has been identified in HPE Application Performance Management BSM Platform versions 9. The vulnerability could be remotely exploited to allow code execution. CVE 2. 01. 7 1. BIDMISCCONFIRMhp bsmplatformapplicationperformancemanagementsystemhealth. A directory traversal vulnerability in HPE BSM Platform Application Performance Management System Health product versions 9. CVE 2. 01. 7 1. MISCCONFIRMAUSCERThp bsmplatformapplicationperformancemanagementsystemhealth. An authentication vulnerability in HPE BSM Platform Application Performance Management System Health product versions 9. CVE 2. 01. 7 1. MISCCONFIRMAUSCERThp ucmdbconfigurationmanager. A potential security vulnerability has been identified in HP UCMDB Configuration Manager versions 1. These vulnerabilities could be remotely exploited to allow code execution. CVE 2. 01. 7 1. CONFIRMBack to top. Medium Vulnerabilities. Primary. Vendor Product. Description. Published. CVSS Score. Source Patch Infoapache geode. When a cluster is operating in secure mode, a user with read privileges for specific data regions can use the gfsh command line utility to execute queries. In Apache Geode before 1. CVE 2. 01. 7 9. MLISTartifex gsview. Artifex GSView 6. Beta on Windows allows attackers to cause a denial of service or possibly have unspecified other impact via a crafted. Possible Stack Corruption starting at KERNELBASE Raise. Exception0x. CVE 2. CONFIRMartifex gsview. Artifex GSView 6. Beta on Windows allows attackers to cause a denial of service or possibly have unspecified other impact via a crafted. Reviews Of T-Tapp Exercise Program. Data from Faulting Address controls Branch Selection starting at mupdfnet. Incremental. Save. File0x. 00. 00. 00. CVE 2. 01. 7 1. CONFIRMartifex gsview. Artifex GSView 6. Beta on Windows allows attackers to execute arbitrary code or cause a denial of service via a crafted. Read Access Violation on Block Data Move starting at mupdfnet. Incremental. Save. File0x. 00. 00. 00. CVE 2. 01. 7 1. CONFIRMblogotextproject blogotext. Stored XSS vulnerability via a comment in incconv. Blogo. Text before 3. Java. Script. If the victim is an administrator, an attacker can for example change global settings or createdelete posts. It is also possible to execute Java. Script against unauthenticated users of the blog. CVE 2. 01. 7 1. MISCMISCMISCMISCcfpaypal cpcontactformwithpaypal. The cp contact form with paypal aka CP Contact Form with Pay. Pal plugin before 1. Word. Press has CSRF with resultant XSS, related to cpcontactformpp. CVE 2. 01. 5 9. MISCMISCMISCcfpaypal cpcontactformwithpaypal. The cp contact form with paypal aka CP Contact Form with Pay. Pal plugin before 1. The Elder Scrolls Oblivion Patch 1.2. Word. Press has SQL injection via the cpcontactformppid parameter to cpcontactformpp. CVE 2. 01. 5 9. MISCMISCMISCcheckmkproject checkmk. CheckMK before 1. GUI crash report. CVE 2. 01. 7 1. CONFIRMCONFIRMegroupware egroupware. Stored XSS vulnerability in e. Groupware Community Edition before 1. Java. Script via the User Agent HTTP header, which is mishandled during rendering by the application administrator. CVE 2. 01. 7 1. MISCMISCfreedesktop poppler. In Poppler 0. 5. 9. NULL Pointer Dereference exists in Annot. Rich. Media Content Content in Annot. PDF document. 2. 01. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. In Poppler 0. 5. 9. NULL Pointer Dereference exists in the Splash. Output. Dev type. D0 function in Splash. Output. Dev. cc via a crafted PDF document. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. In Poppler 0. 5. 9. NULL Pointer Dereference exists in Annot. Rich. Media Configuration Configuration in Annot. PDF document. 2. 01. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. In Poppler 0. 5. 9. Object dict. Lookup in Object. Gfx display, Gfx go, Gfx exec. Op, Gfx op. Fill, Gfx do. Pattern. Fill, Gfx do. Tiling. Pattern. Fill and Gfx draw. Form calls aka a Gfx. CVE 2. 01. 7 1. CVE 2. CONFIRMfreedesktop poppler. The Fo. Fi. Type. C convert. To. Type. Fo. Fi. Type. 1C. Poppler 0. 5. 9. 0 has a NULL pointer dereference vulnerability because a data structure is not initialized, which allows an attacker to launch a denial of service attack. CVE 2. 01. 7 1. CONFIRMfreedesktop poppler. The Fo. Fi. Type. C convert. To. Type. Fo. Fi. Type. 1C. Poppler 0. 5. 9. 0 has a heap based buffer over read vulnerability if an out of bounds font dictionary index is encountered, which allows an attacker to launch a denial of service attack. CVE 2. 01. 7 1. CONFIRMCONFIRMfreedesktop poppler. The Fo. Fi. True. Type get. CFFBlock function in Fo. Fi. True. Type. cc in Poppler 0. NULL pointer dereference vulnerability due to lack of validation of a table pointer, which allows an attacker to launch a denial of service attack. CVE 2. 01. 7 1. CONFIRMgnu binutilsdecodelineinfo in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file. 2. 01. 7 0. CVE 2. 01. 7 1. CONFIRMCONFIRMgnu binutilsreadformattedentries in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file. 2. 01. 7 0. CVE 2. 01. 7 1. CONFIRMCONFIRMCONFIRMgnu binutilsprocessdebuginfo in dwarf. Binary File Descriptor BFD library aka libbfd, as distributed in GNU Binutils 2. ELF file that contains a negative size value in a CU structure. CVE 2. 01. 7 1. CONFIRMCONFIRMgnu binutilsbfdelfslurpversiontables in elf.
